STRATEGIES TO REDUCE YOUR CHANCE OF BUSINESS IDENTITY THEFT
The term identity theft is defined as the deliberate use of someone elses identity, usually as a method to gain a financial advantage or obtain credit and other benefits in the other persons name. These criminals, also called hackers or fraudsters, obtain peoples personal information through various sophisticated and old fashioned methods of stealing, including skimming, phishing, dumpster diving, shoulder surfing, and remote thievery.In all the security issues, companies face, business identity theft is one of the scariest, since it has the power to damage your relationship with key customers and employees. Businesses have been stockpiling more and more personally identifiable information (PII) about customers since the advent of the digital age. PII -- including credit card numbers, social security numbers, birth dates, addresses, etc. -- is often collected in the course of sales, applications for credit or loans, and in the course of employment. This information is often maintained by businesses in computer databases or on disks or is transmitted over networks, such as the Internet. These continued mischaracterizations are dangerous, because they cause businesses and business owners to remain unaware of the true nature and risks of business identity crimes, and unprepared to take appropriate actions to protect themselves.
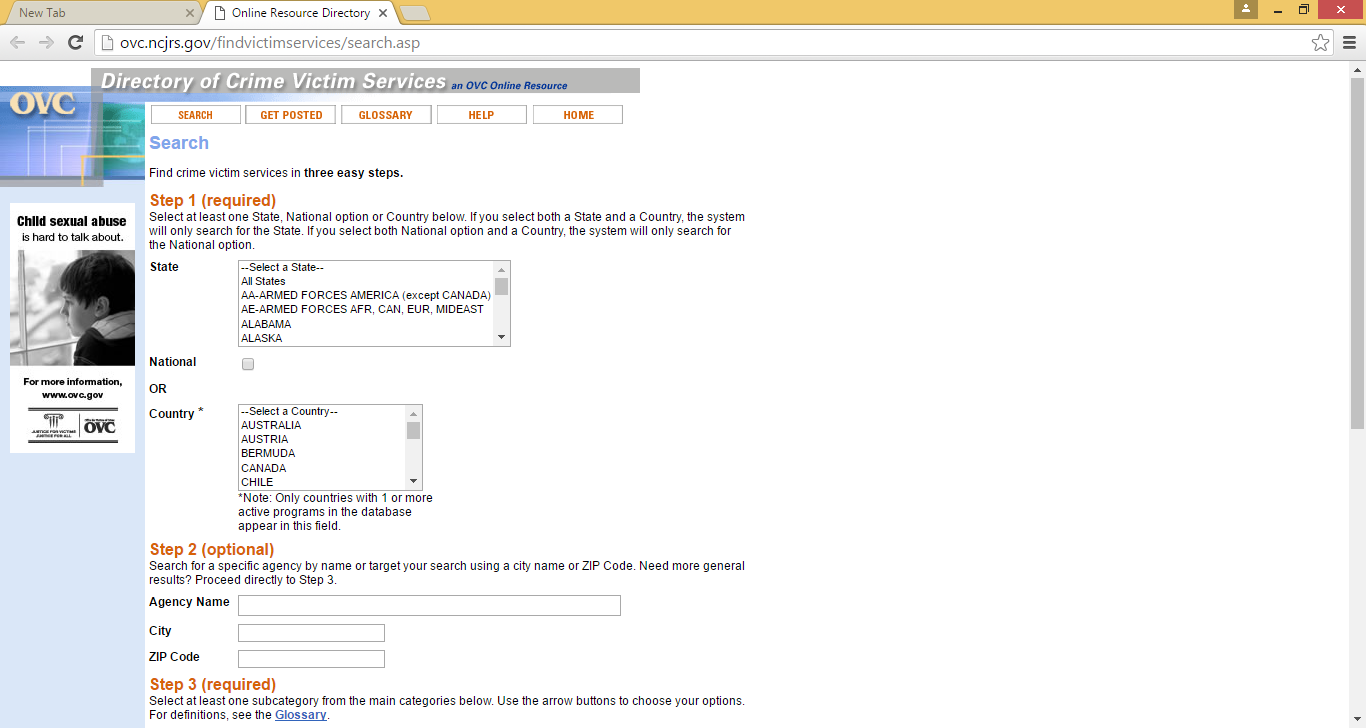
Here's a checklist of strategies that might guide your security decisions to reduce your chance of business identity theft:
OPERATE WITH AN EIN:-
While a corporation or limited liability company must have a separate employer identification number (EIN) for tax identification purposes, a freelancer or small-business owner may operate as a sole proprietorship under his or her Social Security number, even if the business has employees. Just because you can, doesn't mean you should. It's generally a better idea for sole proprietors to use an EIN, which can easily be obtained through the IRS website.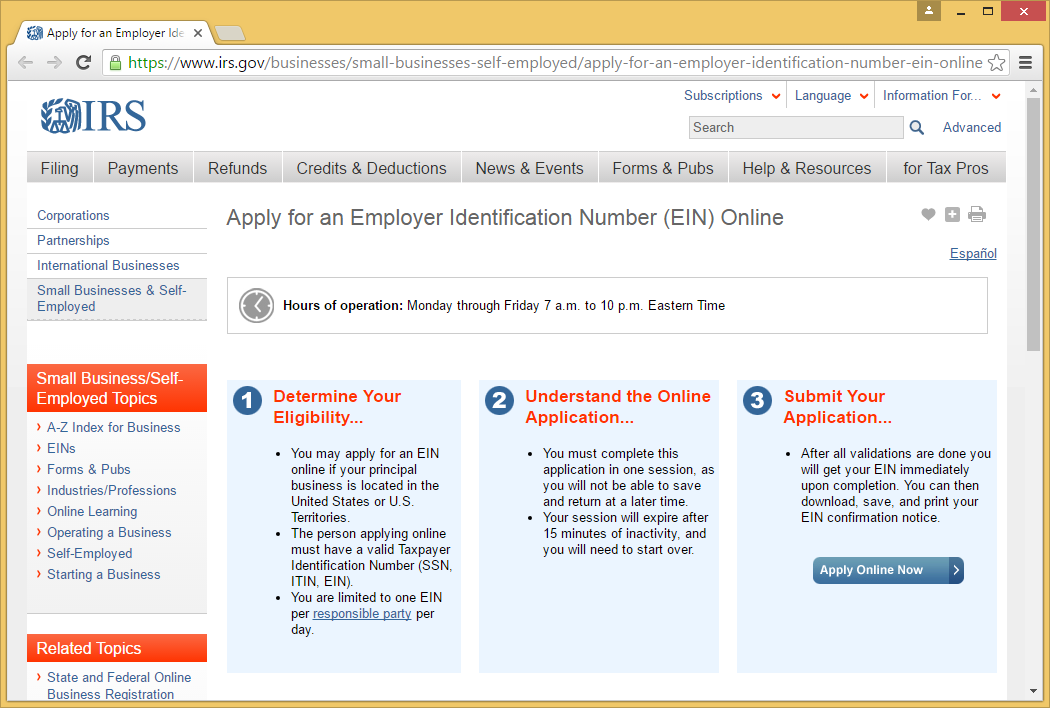 Keeping business and personal finances separate is a good idea for many reasons, including identity theft prevention.
"That protects the business owner."
Keeping business and personal finances separate is a good idea for many reasons, including identity theft prevention.
"That protects the business owner."
ESTABLISH INTERNAL CONTROLS:-
Some of scam relies on an authoritative tone over email or the phone that tricks people into divulging confidential information, such as company account numbers or passwords. Phishing scams often purport to be from government agencies or legitimate financial institutions, even though none of those entities would ever ask a business owner to divulge such information by phone or over email. Businesses with employees need to pay extra attention to security. Its important to use passwords or otherwise restrict employee access to certain documents, such as customer lists or accounting files. Establish a clear protocol to follow in the event of a data breach, including assigning someone to manage the breach and outlining what actions are needed to be taken. For retail businesses, business owners review security footage for suspicious activity, such as an employee taking a customer's card away from the register to run a transaction.CHECK YOUR COMMERCIAL ACCOUNT STATEMENTS REGULARLY:-
Keeping an eye on your accounts is one of the best methods of halting fraud before it gets out of hand. Experian and other credit reporting agencies offer monitoring services that can help. Review your banking agreements to determine whether your business accounts have protection against fraud, which can differ from consumer protections. In addition, review your insurance policies to see what, if any, coverage you have in case of a data breach that exposes customer information or if you incur other losses from fraud or ID theft. If a company has a longstanding relationship with a bank, it's worth having a conversation with bank officials to let them know that there are no plans to open new lines of credit or loan accounts.KEEP PHYSICAL DOCUMENTS SAFE:-
Keep all your company documents and records in a safe and secure location. Safes are built for the purpose of keeping your documents and files safe from prying eyes with malicious intent. When throwing away documents that contain sensitive information, its best to shred the file to prevent it from getting in the wrong hands. Never provide your companys federal tax identification number, financials, or bank statements to anyone unless you have made the initial contact. . Dumpster diving is a common method of stealing where criminals search the trash for items of use and value.FILE ANNUAL REPORT ON TIME:-
Incorporated companies are required to file annual reports in most states. These are simple documents that keep the state up to date on basic information about your business. When a company fails to file an annual report on time; it may face administrative dissolution from the state. This means it is no longer considered incorporated in that state and can face fines if it remains in business without properly registering. It can also mean that the company loses access to the states courts, among other legal protections. In addition, businesses that fall into administrative dissolution wind up on state lists of inactive companies. By utilizing a different mailing address, criminals can work to get the company reinstated without the owners knowledge. They can then receive a certificate of good standing for the business, with which they can open up lines of credit or order merchandise that can easily be resold.PUT A SECURITY FREEZE ON YOUR CREDIT PROFILE:-
Closing any compromised credit and bank accounts can stem your financial losses, true. But thieves can continue opening false accounts and piling up debt on your credit profile, making it impossible to successfully apply for credit. To stop thieves in their tracks, put a security freeze on your credit profile, which prohibits lenders and companies that are trying to check your credit from accessing your profile. This prevents thieves from opening new accounts under your name, because creditors are unable to check your credit history. The security freeze is a good tool for someone with recurring fraud issues.PUT CUSTOMERS ON ALERT:-
Create invoicing standards with customers, and ask them to check with you if there are any changes. For example, you may regularly email invoices and accept electronic payments. If a customer gets a mailed invoice with a request that a check or money order is sent to a location that's different from the company address that should be a red flag. By monitoring accounts frequently and being more aware of potential threats, a business can reduce the chances that identity thieves will do long-term damage.PURCHASE AND UPDATE SECURITY DEVICES OR SOFTWARE:-
Many companies tend to purchase security devices or software, but then take a "set it and forget it" mentality that pushes the issue to the back burner. "A standalone device purchased only a year ago that hasn't been updated or monitored may already be breached, and you wouldn't even know it." So make sure that you update it regularly. Links from scams usually have viruses that can infect your computer and become gateways for hackers to control your device. When choosing a security device, its always wise to avoid nefarious applications masquerading as free device or software. For safety measures, always choose popular programs trusted by a lot of people.BE CAREFUL ABOUT ONLINE SECURITY:-
Business owners should not ignore what's being said online about their companies. This practice can lead to trouble or it could also be that someone has updated the company's business information. Take a proactive approach to online reputation management and build it into the business plan and marketing strategy. Check the sites regularly, include Yelp and Google.Beware of suspicious links and attachments in your email. Some thieves will send victims emails containing links that may appear to be from a legitimate source. However, these links are often directed to a fake site designed especially to collect sensitive data, such as peoples usernames and passwords. Usually, criminals send these emails during holiday seasons alongside promotional emails from other legitimate or popular websites.
If a company uses wire transfers and electronic payments, it's wise to implement a system that requires at least two people to approve each transfer. Some financial institutions also offer other forms of authentication that must be provided before a transfer is approved.
You might want to think twice before you connect to a public Wi-Fi. Sometimes, cyber fraudsters will hack and use public Wi-Fi to access private data on their victims devices. They can do this easily by using a technique called sniffing that intercepts data packets and enables the user to see everything on a fellow free Wi-Fi users device.
HELPFUL RESOURCES AT THE TIME OF BUSINESS ID THEFT:-
Business ID theft can be particularly difficult to investigate. But the good news is that federal, state, and local law enforcement authorities are becoming more sophisticated about and devoting more resources to responding to business identity theft.LOCAL LAW ENFORCEMENT:-
Even if you have been the target of a multijurisdictional identity theft, your local law enforcement agency (either police department or sheriffs office) has an obligation to assist you, take a formal report, and make referrals to other agencies, when appropriate. Report your situation as soon as you find out about it. Some local agencies have detectives or departments that focus specifically on cybercrime.IC3:-
The Internet Crime Complaint Center (IC3) will thoroughly review and evaluate your complaint and refer it to the appropriate federal, state, local, or international law enforcement or regulatory agency that has jurisdiction over the matter. IC3 is a partnership between the Federal Bureau of Investigation and the National White Collar Crime Center (funded, in part, by the Department of Justices Bureau of Justice Assistance). Complaints may be filed online at ic3.gov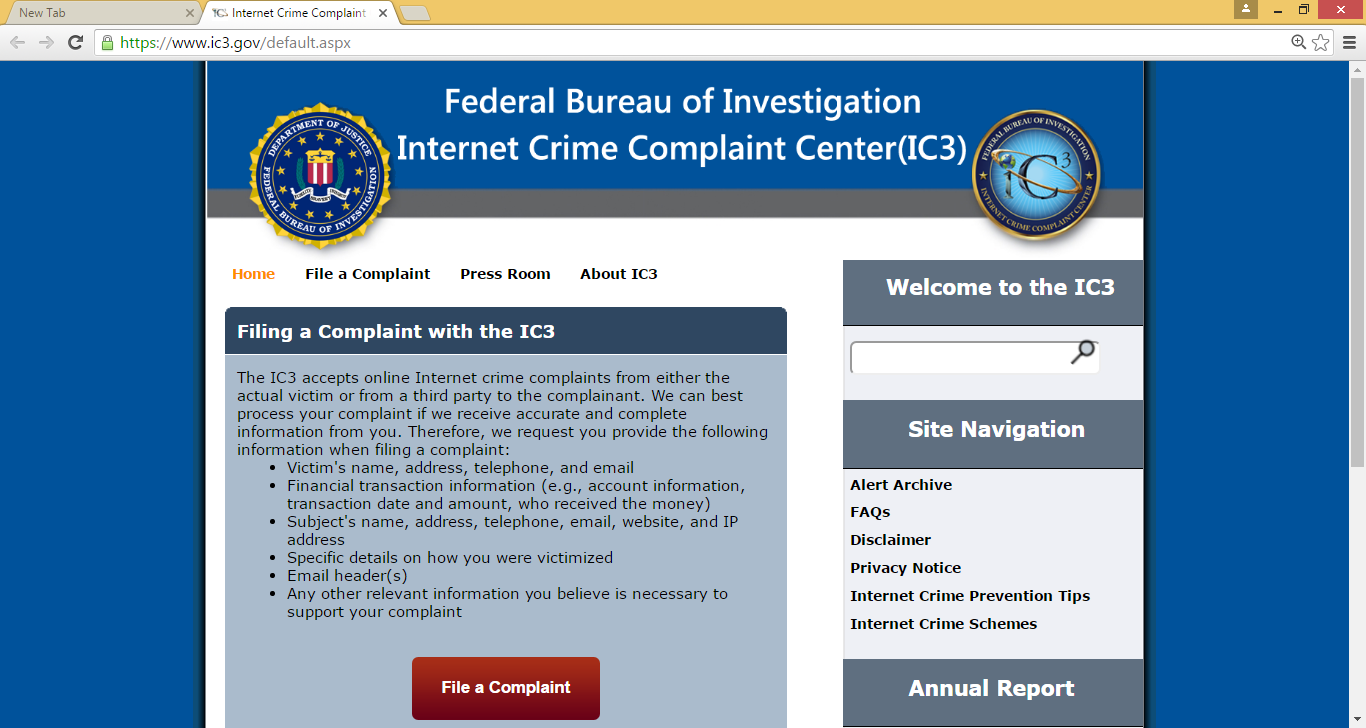
FEDERAL TRADE COMMISSION (FTC):-
The FTC does not resolve individual consumer complaints, but does operate the Consumer Sentinel, a secure online database that is used by civil and criminal law enforcement authorities worldwide to detect patterns of wrong-doing, leading to investigations and prosecutions. File your complaint at ftc.gov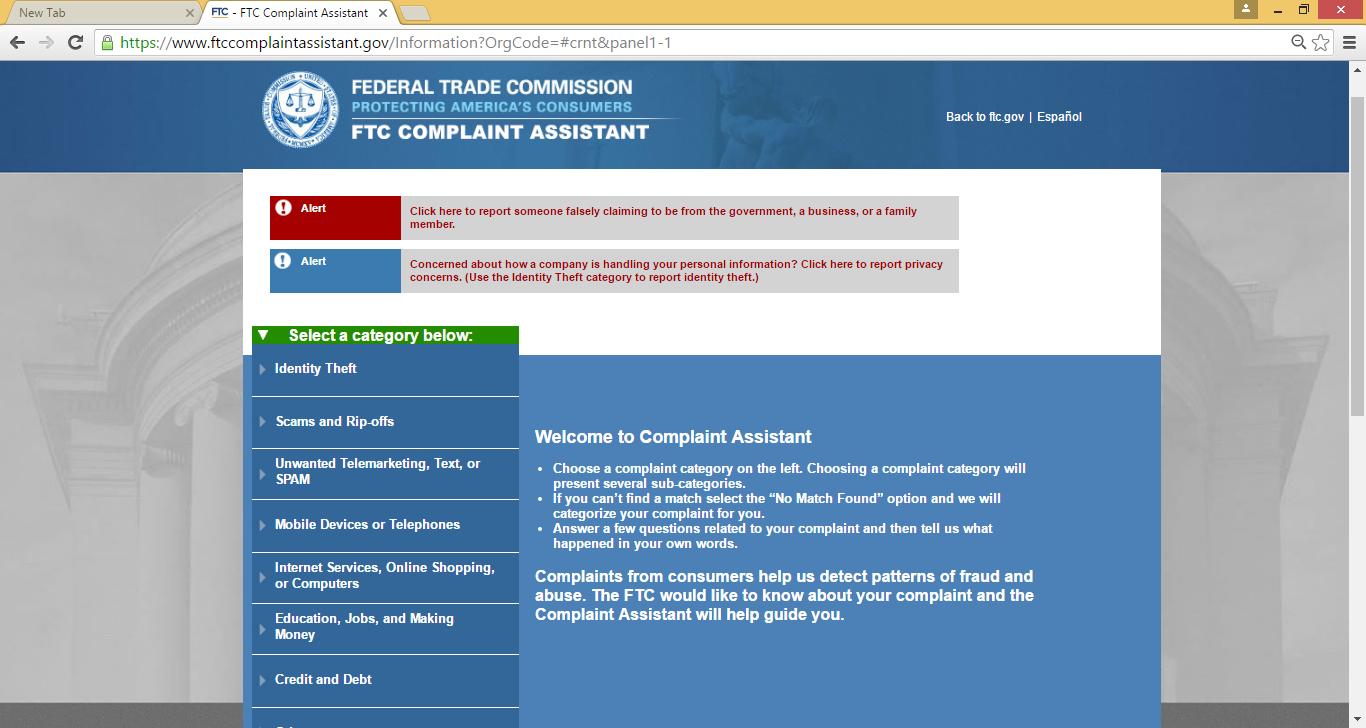
YOUR LOCAL VICTIM SERVICE PROVIDER:-
Most communities in the United States have victim advocates ready to help following a crime. They can provide information, emotional support and advocacy as needed. Find local victims service providers here: